VPN Concentrator: What Is It and How It Works
The vital role of VPN concentrators
Security has become a leading topic when it comes to companies strategising a future of employees working remotely from all around the world. As the COVID-19 pandemic has made topics like work from home more popular, the issue has been amplified.
Whether a company deals with sensitive medical information, financial documents, or any other proprietary information that needs to traverse the network highways, getting said data from A to B safely is a key task for today’s IT professionals. While virtual private networks (VPNs) can encrypt data for transport and have done so for 25 years, VPN concentrators are essential for managing the flow of users and data encryption for distributed organisations.
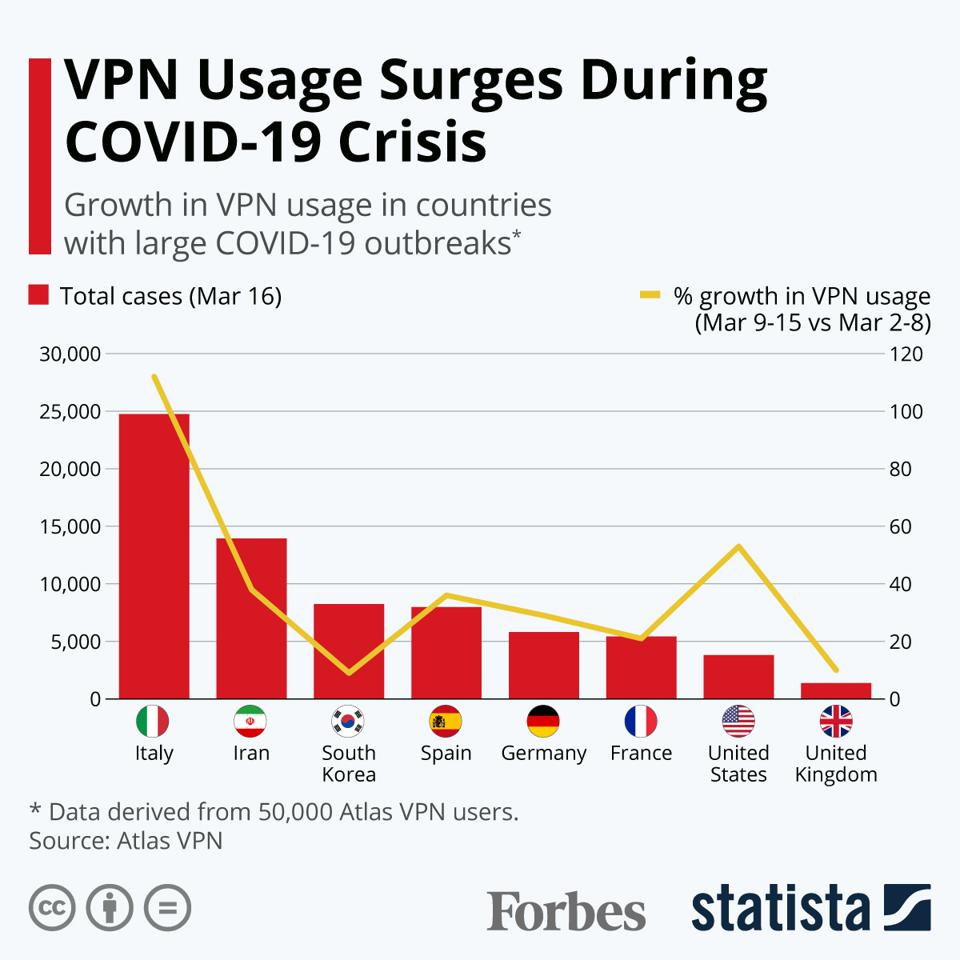
(Image: Forbes)
As we can see from the chart above, VPN usage has surged within countries that were significantly affected by the COVID-19 outbreak in early 2020. As more businesses switched to remote work, VPNs offered an essential layer of security to keep documents safe from prying eyes.
However, despite a rise in VPN use cases, there’s still some confusion as to the role of VPN concentrators, and the vital role they play. With this in mind, let’s take a deeper look into this essential tool and how it can help to keep businesses more secure in a remote future:
So, What Actually is a VPN Concentrator?
How VPN concentrators work is by creating many VPN tunnels simultaneously whilst offering a fully encrypted, private connection between various VPN nodes. This means that VPN concentrators establish various CPN connections remotely while helping to manage them at the same time as a server-side function.
These concentrators serve as an extension of the capabilities of a VPN router. VPN concentrators are an effective tool for delivering service to hundreds or thousands of users, with a dedicated tunnel assigned to all of them. Larger businesses or organisations can use VPN concentrators to help all of their workers or members to connect to the company’s home network from any location across the globe.
Coming in the form of a piece of hardware, VPN concentrators operate in a similar way to typical VPNs in that they also encrypt the data that users receive and omit across the internet, but the device does this on a much larger and more distributed scale.
VPN concentrators are extremely powerful and resourceful tools in distributed scenarios, and because of this, the devices are rarely used privately – rather they are utilised by larger businesses, often with more remote employees. You may also find VPN concentrators in large organisations like the military.
The Differences Between a VPN Concentrator and a VPN Router
VPN concentrators aren’t to be confused with VPN routers. Both devices operate in similar ways but there are some distinct differences to take into consideration.
The concentrator can take on many thousands of users simultaneously while creating a VPN tunnel for each of them, making it perfect for corporate environments where the employees can safely connect to their company network from any remote location. However, a VPN router is meant to be used for home networks or small businesses where only a handful of users have access to the private network.
Besides supporting more users, VPN concentrators also have more advantages over their router counterparts. More modern concentrators utilise highly effective firewalls and also uses advanced encryption techniques, data encryption, the development VPN tunnels, authentication protocols for multiple users and assigning tunnels for each connected user.
The Purpose of VPN Concentrators
VPN tunnels that are created are managed by VPN concentrator protocols. These devices cover the complete network of outgoing data and convert them all into encrypted packets before it eventually maneuvers it all through the tunnel. By doing this, the VPN concentrator can decrypt, de-encapsulate and receive converted data.
Concentrators can also cover user authentication and has the ability to set up IP addresses for everybody on the network whilst also creating and managing cryptographic keys.
Because of its function, some people may be led to believe that VPN concentrators are similar to commonplace routers, but they can also bring users a more comprehensive level of privacy to the flow of network traffic. This makes concentrators vital for companies that may be looking to make a transition to more work from home business models in the wake of the COVID-19 pandemic, or for businesses looking to support large volumes of distributed employees on a single network.
Assessing The Pros of VPN Concentrators
Concentrators allow business or organisation networks to be connected to safely and privately from anywhere across the globe. Once the concentrator is done working on encrypting connections, it transmits data and various requests to the business server via an especially encrypted VPN tunnel. These tunnels are generated instantaneously once it’s requested by the individual user.
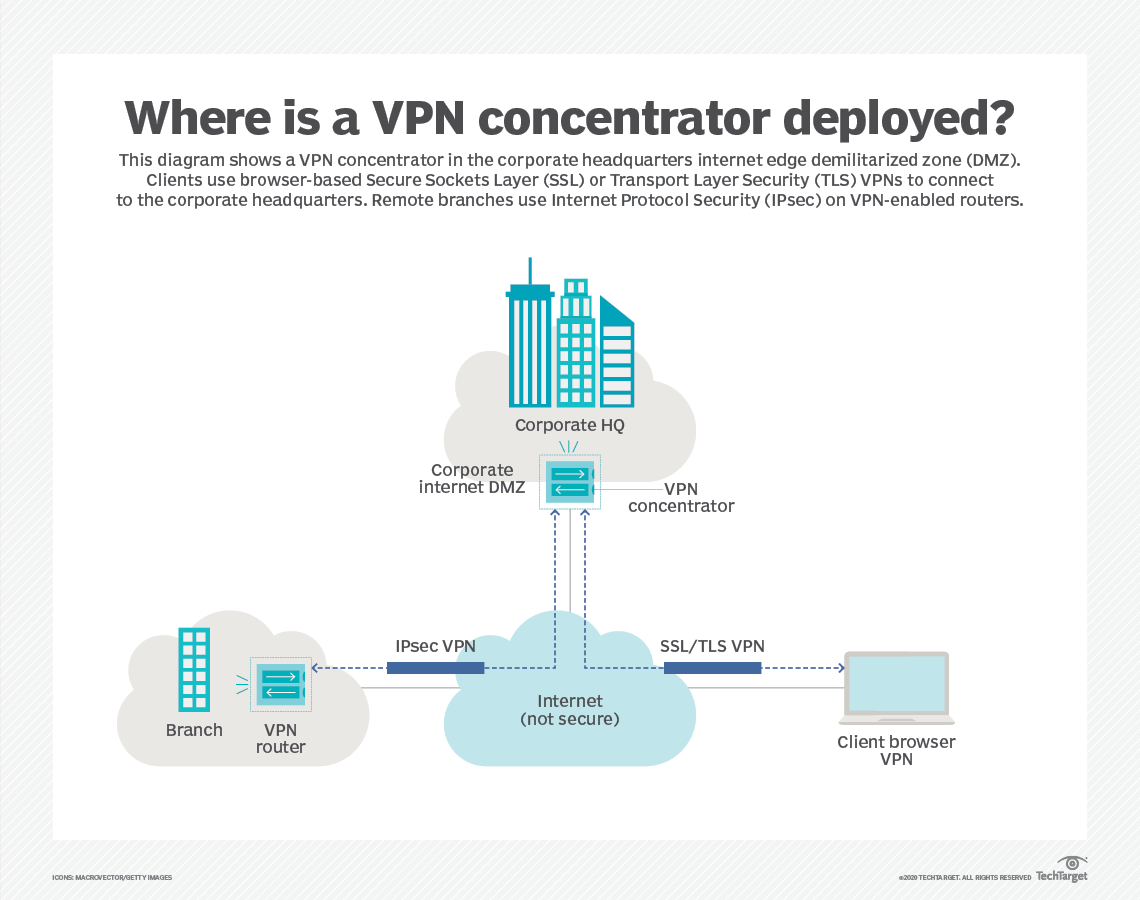
(Image: Search Networking)
Although concentrators can be used in any distributed organisation, let’s look at how it works in a more business sense. As we can see from the diagram above, VPN concentrators play a valuable role in the deployment of private data between a corporate HQ and its various branches and client browsers.
Interactions with company software can instantly develop new tunnels through the use of the VPN concentrator so that users can immediately access data securely. Software apps can also be set up on an ‘always-on’ basis which enables encrypted tunnels to constantly be available when called upon.
The biggest perk that VPN concentrators offer is that they provide peace of mind against hackers who could potentially infect distributed computers with malware or spy on sensitive information. The levels of encryption generated by the tunnels that VPN concentrators make can be essential when security is of the essence.
Although a VPN router could still do a perfectly fine job at a small business with very few distributed workers, large companies may require concentrators to secure the data passed between company servers and staff working from home.
Despite concentrators and routers behaving in similar ways, it’s important to avoid confusion between typical routers and VPN concentrators. The advanced protocols and algorithms that concentrators can utilise to shore up business communications can be essential in keeping data safe. While this may be a common mistake to make for business owners, the significantly larger volumes of protection that concentrators are capable of offering make VPN concentrators an essential choice for remote businesses.